2025-01-07 New DNS Firewall Feed Protects Polish Users from Data Theft!
Today, the ioc2rpz community is excited to announce the addition of a new DNS Firewall feed – certpl.ioc2rpz!
This feed, maintained by cert.pl (https://cert.pl/en/warning-list/), provides a critical line of defense for Polish internet users. It contains a comprehensive list of dangerous websites known to trick users into surrendering their data and credentials.
Double Protection with malicious.ioc2rpz
In addition to the dedicated certpl.ioc2rpz feed, this valuable data has also been integrated into the existing malicious.ioc2rpz combination feed. This ensures even broader protection for users who rely on the combined threat intelligence provided by malicious.ioc2rpz.
By leveraging these feeds, users and organizations in Poland can significantly reduce the risk of falling victim to phishing attacks and other malicious online activities that target their personal information.
Stay Safe Online!
If you're a DNS administrator or concerned about online security in Poland, we encourage you to explore the ioc2rpz community and learn how to implement these valuable feeds to protect your users and data.
2024-09-21 Custom feeds depreciation
"Custom feeds" is a nice feature but not used a lot by the community. It's currently running on a dedicated server and it's not worth spending almost $40 monthly just for it. The community portal will be updated soon to reflect the changes.
Please remove any custom feeds from your server's configuration. If you have any questions, please contact me via Telegram chat.
2023-10-05 notracking.ioc2rpz and notracking-dead.ioc2rpz are deprecated
On June 26 2023, the maintainer of notracking feeds decided to EoL the project. The feeds no more accurate and will be removed from ioc2rpz community on October 26 2023.
We recommend to migrate to oisd feeds (oisd-basic.ioc2rpz, oisd-full.ioc2rpz, oisd-nsfw.ioc2rpz).
2023-07-03 RpiDNS on Raspberry PI OS 11 and Ubuntu 22.04
RpiDNS is now supported on Raspberry PI OS 11 (32 and 64 bits) and Ubuntu 22.04 (64 bits).
2023-06-26 The right to be forgotten
ioc2rpz community cares about your privacy and personal data. We do not:
- put any ads or trackers on the portal;
- collect personal information and the registration form is pretty basic;
- logs are timely rotated.
And we just released a very important feature - "delete profile". We welcome all our users but understand that sometimes you may need to unsubscribe (it is possible) or completely to delete profile. The action is irreversible and with your credentials the following items will be removed: logs, rpidns, your tsig key, your custom RPZ feeds, AWS subscription. So we recommend check the transfer logs and reconfigure all your DNS servers which use ioc2rpz community feeds before you remove your profile.
2023-04-17 New DNS Firewall feed - blox-malicious.ioc2rpz, deprecation of blox-ukraine-russia-conflict.ioc2rpz and blox-turkiye-earthquake.ioc2rpz feeds
New DNS Firewall feed blox-malicious.ioc2rpz is powered by Infoblox's Threat Intelligence Group (TIG). TIG detects, curates, and publishes threat intelligence data pertaining to relevant cyber campaigns. TIG is sharing indicators of compromise (IOCs) related to threats that are of high interest to the cyber security community through this public repository.
The feed includes all shared malware, phishing, scams, suspicious domains, DDGA, malvertising, smishing domains including newly identified DNS beacons (a variant of an open source RAT called Pupy) connecting to Russian C2s.
The feed also includes IoCs related to the war in Ukraine and earthquake in Türkiye so blox-turkiye-earthquake.ioc2rpz and blox-ukraine-russia-conflict.ioc2rpz will be deprecated on June 1st 2023.
2023-02-27 New DNS Firewall feeds: shreshta-nrd-1w.ioc2rpz, blox-turkiye-earthquake.ioc2rpz, oisd-nsfw.ioc2rpz
ioc2rpz community got 3 new feeds:
- shreshta-nrd-1w.ioc2rpz - SDINET Newly registered domain(NRD) feed contains a list of domains which were recently registered in com, net, se, info, xyz, nu, sk, ee, link, top, org, ch TLDs. The community feed is delayed by 24-48 hours and records expire in 7 days. The feed is provided by courtesy of Shreshta IT (https://shreshtait.com).
- blox-turkiye-earthquake.ioc2rpz - Malware, phishing, scams, suspicious domains related to the earthquake in Türkiye. The feed is provided by Infoblox's Threat Intelligence Group (https://github.com/infobloxopen/threat-intelligence).
- oisd-nsfw.ioc2rpz - oisd nsfw domain feed to block Shock / Porn / Adult content. The feed is powered by https://oisd.nl To report false positives, please use the following form https://oisd.nl/reportfalsepositive.
shreshta-nrd-1w.ioc2rpz and oisd-nsfw.ioc2rpz are policy feeds, assess their impact before provisioning in a blocking mode.
2023-02-21 ioc2rpz community service update
ioc2rpz community cares about your privacy and reducing number of unnecessary communications. The service is evolving and we have to post notifications about maintenance, deprecated or new features and feeds.
This this release ioc2rpz community will start emailing service notifications and news. If you don't like to receive them, you have an option to opt out in the settings.
Just to recap, last year we added 2 new feeds: "blox-ukraine-russia-conflict.ioc2rpz", "hblock.ioc2rpz" and early this year an integration with AWS Route 53 DNS Firewall (and actually Pi-hole).
Later this month we will be releasing 3 new feeds - stay tuned for the updates.
The following community portal upgrade will be focused on removing inactive accounts. You will receive an email notification if your account is scheduled for removal. The details will be posted with the feature release.
2023-01-17 ioc2rpz community feeds for AWS Route 53 DNS Firewall
I'm happy to announce a tight integration of ioc2rpz community portal with AWS Route 53 DNS Firewall.
With Route 53 Resolver DNS Firewall, you can filter and regulate outbound DNS traffic for your virtual private cloud (VPC). To do this, you create reusable collections of filtering rules in DNS Firewall rule groups, associate the rule groups to your VPC, and then monitor activity in DNS Firewall logs and metrics. Based on the activity, you can adjust the behavior of DNS Firewall accordingly.
ioc2rpz community provides OSINT based filtering rules via files on AWS S3. You will need to periodically update Route53 domain lists (e.g. with a lambda function).
The integration requires a subscription which is available on AWS Marketplace. There are 4 tiers: free, core (includes free), essentials (includes core), standard (includes essentials) with a minimal price tag (like a donation).
2022-09-16 3 years anniversary!
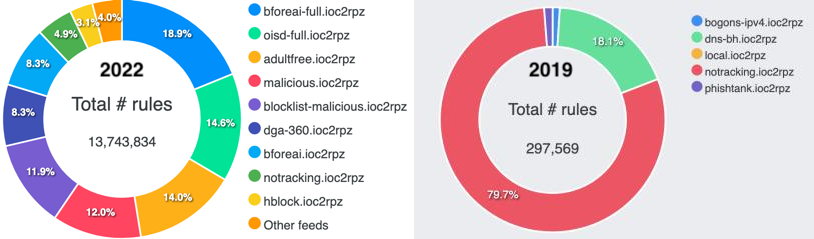
I'm a bit late with my post but I want to share that in August the ioc2rpz community website (https://ioc2rpz.net) celebrated its 3 years anniversary.
Back when it had just 5 feeds with about 300k rules and now the community portal serves 18 feeds with over 13M rules not counting user defined TLD and country feeds. The community feeds (mostly based on OSINT) include malicious and phishing websites, adult content, ads and tracking domains filters. Bfore.Ai's crime prevention predictive feed protects against newly registered, potentially phishing domains.
If you are interested in some statistics, the community website serves users from all continents except Antarctica (I wish that someone can spin up RpiDNS here :), 41 countries and 109 locations. The most downloaded feeds are: dga-360.ioc2rpz, doh.ioc2rpz, phishtank.ioc2rpz, urlhaus.ioc2rpz, blocklist-malicious.ioc2rpz and notracking.ioc2rpz
The community is non-profit and kind of my hobby so I don't really have a lot of time for maintenance. Luckily ioc2rpz technology (http://ioc2rpz.com, my open source project) was built on Erlang and robust enough so it doesn't really require a lot of care. If you want to know how to deploy it in your enterprise/ISP DM me.
The community is open for new users and if you want to protect your home, home office or even office a Raspberry Pi with community feeds can easily handle this task.
News | ioc2rpz technology | Terms & conditions | Donate | Contact us
Sign up
Sign in
Email confirmation
Restore password
Change password
Thank you for subscribing to ioc2rpz feeds!
Sign in/up on the community portal to access provisioning information on AWS Route53 Feeds page. Step by step instructions are available in the help.